A while back Microsoft introduced the ability to use Third party Mobile Device Management compliance data for Intune and Azure AD device compliance and therefore Azure AD Conditional Access.
Obviously the recommendation is to use Intune for Mobile Device Management, but there might be scenarios where that is not possible for whatever reasons. It is very welcome news that finally we are able to recognize 3rd Party managed devices as compliant and utilize Conditional Access policies fully.
In this blog post I will go through the pre-requisites and configurations that are needed in the backend for
- Workspace One
- Azure AD
- Intune
I will also show the end user experience on Workspace One managed Android device.
Pre-Requisites
- Enterprise Integration for Workspace One. Meaning one of the following
- Cloud Connector for AD
- SAML Connector for Azure AD
- Workspace One Intelligence Opt-in
- Device enrolled to Workspace One MDM
- Azure AD Conditional Access Policy to require Compliant Device when using Apps
The important thing here is that the user identity cannot be stand alone in Workspace One in order for this to work. In our example configuration we have the Cloud Connector for AD in place and Enterprise Integration configured using LDAP Directory Type.
Configurations on the back end
The order of the configurations is somewhat meaningful so I will not categorize configurations by platform, but rather go through the configuration process as it happens
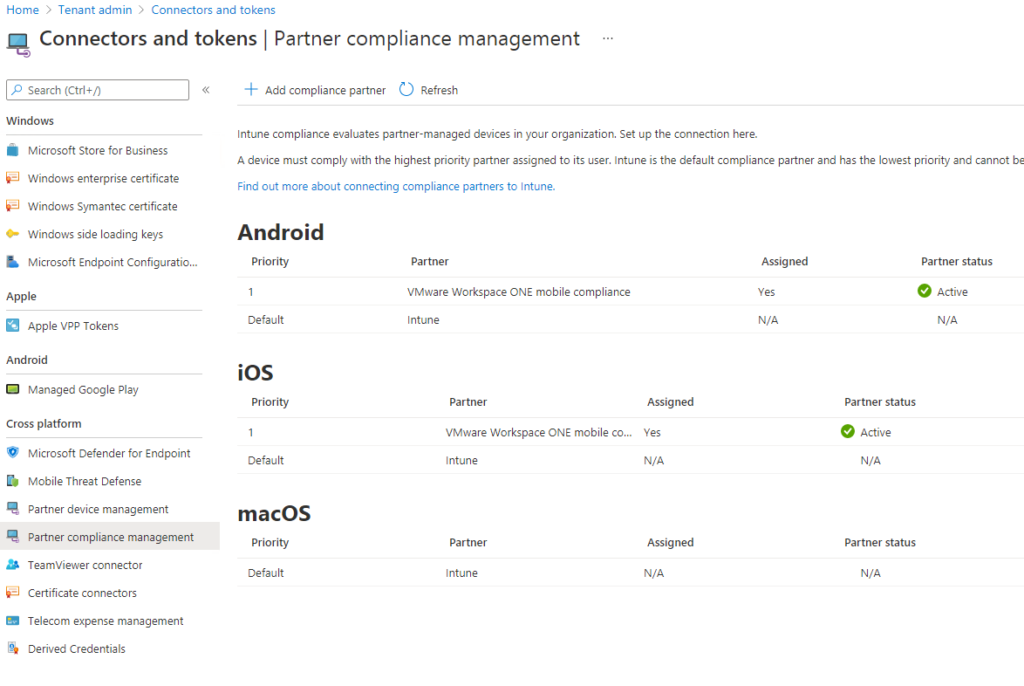
Step 1: Configure Compliance Partner in Intune
Go to Tenant Administration -> Partner Compliance Management and add Compliance Partners for the necessary platforms. In this example we add Compliance Partners for Android and iOS. In this example the Partner we choose is “VMware Workspace ONE mobile compliance”. Also Assign the Compliance Partner configuration to a group of users you want to enable this feature for. I recommend assigning to test user group first.
Step 2: Enable Azure AD Integration
From Workspace One Management Portal menu select settings and go to Enterprise Integration -> Directory Services and enable Azure AD Integration from “Advanced” section. You will need to provide Azure AD Directory ID for this.
Also Enable Azure AD For Identity Services. The wizard will then instruct to add Airwatch Application to Azure AD Tenant and provide you with the URLs you configure in the Application
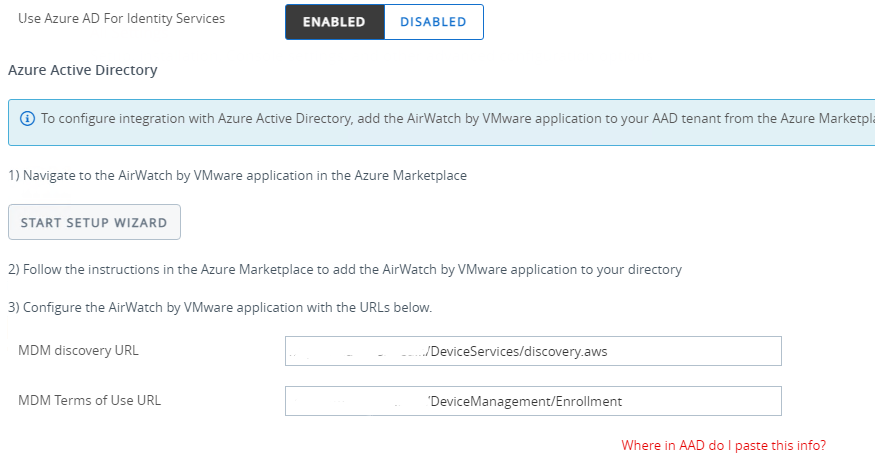
Step 3: Configure the Azure AD Airwatch Application
At this stage what we configure is actually the Mobility (MDM and MAM) Application in Azure AD rather than Enterprise Application.
Go to Azure Active Directory -> Mobility (MDM and MAM) and Add “Airwatch by VMware” Application to the list where you already probably have Microsoft Intune
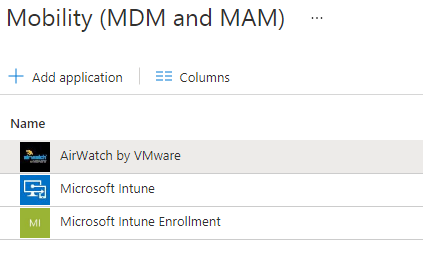
Configure AirWatch Application by entering the URLs that you got from the Azure AD Integration Setup Wizard. Leave MDM User scope to “None”.
Step 4: Proceed the setup wizard to configure Compliance data integration
Enter Tenant name and Immutable ID Mapping Attribute that you can check from Azure AD Connect settings if you dont know what it is.
Enable the user of Compliance Data in Azure Conditional Access Policies and select whether you want to use it for Windows and/or iOS and Android
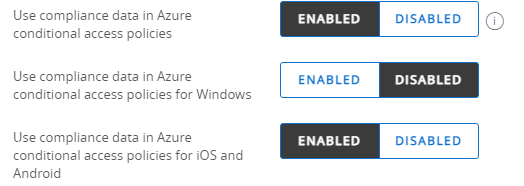
Step 5: Configure Workspace One Conditional Access Application in Azure AD
For Conditional Access and the Compliance data integration to work you will need to add an Enterprise Application to Azure AD.
Go to Enterprise Applications and Add new called “Workspace ONE Conditional Access”. Check that the Application is Enabled for Users to Sign In. Configuration changes for Application are not needed.
Step 6: Exclude “Workspace ONE Conditional Access” Application from applicable Conditional Access Policies.
The same way you would exclude Intune from Conditional Access Policy in order to prevent “chicken – egg” effect. Meaning that you dont want to require Compliant device for the actual enrollment because the device cannot be compliant before it is enrolled.

Step 7: Complete the setup wizard to configure Compliance data integration
Configure the remaining options and run Sync with Azure Services and then save the Enterprise Integration Directory Services configuration.
Step 8: Deploy Microsoft Authenticator App to Devices
In order to be able to transport Compliance Data from Device to Azure AD Microsoft Authenticator App is needed on the device. You should deploy this from the Workspace One as well as Applications you want to test Conditional Access with. These could include Microsoft Teams and Outlook.
End User Experience
As in every aspect of IT the end user experience is what matters most. In this scenario it is not the smoothest possible, but it works. You have a mobile device that is enrolled to Workspace One and you Configure Azure AD Conditional Access Policies so that Compliant device is required to use for example Outlook and Teams.
Here we go. Trying to open Teams App
- Sign In
- Get message saying you need to Enrol the device
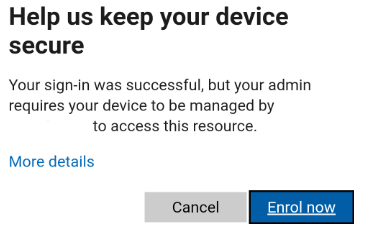
3. Get redirected to Workspace one Microsoft Account connection page. NOTE: This is the only way to connect MS Account to Workspace One Intelligent Hub. So you NEED to have Conditional Access policy requiring the enrollment

4. Get message saying that Hub is connecting with Microsoft Authenticator. This is why you need to deploy MS Authenticator App to the device beforehand. You dont need any configurations in the App

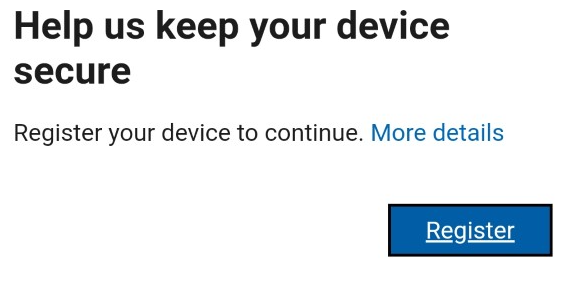
5. Get another message that you should register the device.
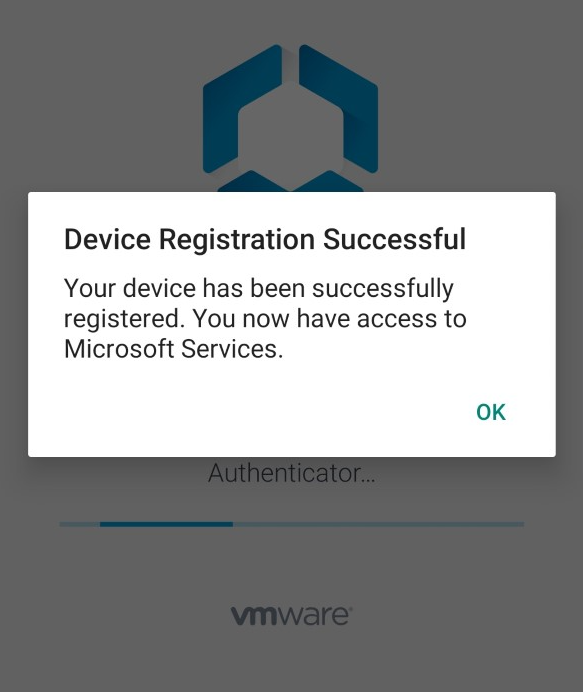
6. Get confirmation that Device Registration was successful and you now have access to Microsoft Services
7. Victory!
Troubleshooting
What if it does not work? As always first check the Azure AD Sign In logs. You should see something like this there if everything went as planned
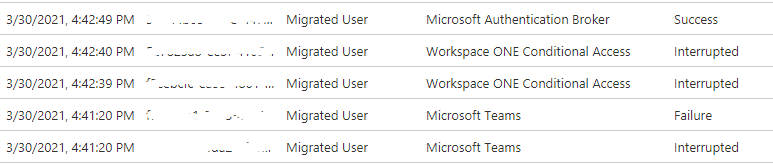
So first you will have the Sign in Attempt to Teams interrupted and failed because Compliant Device is required. Then you are redirected to Workspace ONE Conditional Access App and you get couple of Interruptions before Microsoft Authentication Broker gives you the final green light.
If you for example forgot to Exclude Workspace ONE Conditional Access App from Conditional Access Policies then you might get something like this in the logs:
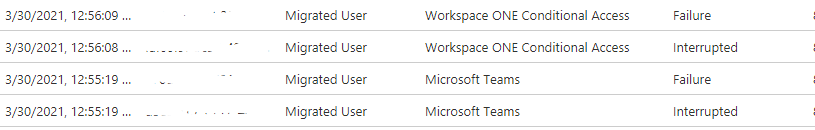
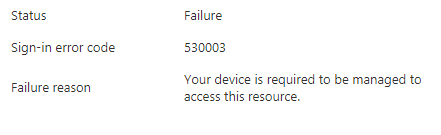
Here the Workspace ONE Conditional Access fails because Conditional Access policy requires Compliant Device aka the “egg-chicken” effect.
Summary
It might not be totally invisible to end users, but at least it does the trick. Meaning that you can now deploy Conditional Access Policies and include devices that are not necessarily managed by Intune or Hybrid Joined to Azure AD.

4 Comments
UEM Testing · 16.06.2021 at 18.35
Thanks for the great post. Really useful! Do we always have to use microsoft authenticator with this or can we use other authenticator apps such as google authenticator?
Matti Väliniemi · 08.09.2021 at 08.46
Hi. Sorry for the late response. Any Authenticator app should work.
Nick · 10.09.2021 at 21.48
Quick Question… When the user is using Edge Browser for iOS, and they are redirected to the Workspace one Microsoft Account connection page. Tapping on “Connect Now”, does not do anything. It works fine in Safari, but not Edge (which is the default browser for the user). Any idea why this would happen?
Adam Tyler · 03.02.2022 at 20.19
Thanks for the information, we are just onboarding some M365 services and really want to leverage the conditional access policies on mobile devices. Without having to migrate MDM providers. Is there any risk involved to turning on “Azure AD Integration”, “Use Azure AD for Identity Services”, and “Use compliance data in Azure conditional access policies for IOS” on our existing Workspace One environment? Can we narrow the scope of the mobile devices that are used with Intune or do we have to get an Intune license for every device enrolled in our WorkspaceOne environment?