Best way to prevent password leaks is to go passwordless
Social engineering and technical tweaks compromise credentials every day. There have been methods to overcome these problems but they were too complicated for larger adoption until now. Does somebody remember the rise of smartcards? I do and I’m happy that I don’t need to work with those solutions anymore. If you are working in Microsoft ecosystem with Azure AD based identities, there is very easy way to improve your security enormously. Start your journey to passwordless today.
I see three key reasons to go passwordless
- Passwords can be used anywhere by anyone
- Passwordless requires a physical proof of presence
- Reduce amount of password resets and service requests for password related problems
Passwordless is and is not same as multi factor authentication. This is most misunderstood thing. Passwordless is strong authentication method that require two factors (something you know, something you are, something you have). Passwordless is not used as second factor after username and password combination as then the whole point loses it’s meaning.
Passwordless building blocks
In Azure AD identity framework, there are three different solutions to go passwordless. Each of those complement each other and there is not only one solution for all the needs. Passwordless environments utilizes Authenticator App, Windows Hello and FIDO2 keys.
Windows Hello is for user to logging in to personal computer and services using personal computer. Identity is stored in computer, is not transferrable and secured using pin or biometrics.
Authenticator App can be used logging in services while using mobile device or another computer than own. Identity is stored in mobile device, is not transferrable and secured using pin or biometrics.
FIDO2 based security keys can be used for logging in to computers and services on other computers and doing first login to new computer. Identity is stored in FIDO2 key, is not transferrable and secured using pin or biometrics.
Getting started
When staring your passwordless journey, you should first do little planning on strategy. How you onboard existing and new users to solution? Technically this is very easy process, but users require some training or information on change that is going to happen.
Microsoft sees this journey as 4 step process
- Deploy password-replacement offerings
- Reduce user-visible password surface area
- Transition to passwordless deployment
- Eliminate passwords from identity directory
Some has already happened for all of us. For instance, have you noticed that when logging to Microsoft 365 services, there is only prompt for username – not for username and password. Therefore, step 2 has already happened here. Microsoft have reduced user-visible password surface area. After inputting your username, one could get prompt in authenticator to verify login and not to see password prompt at all.
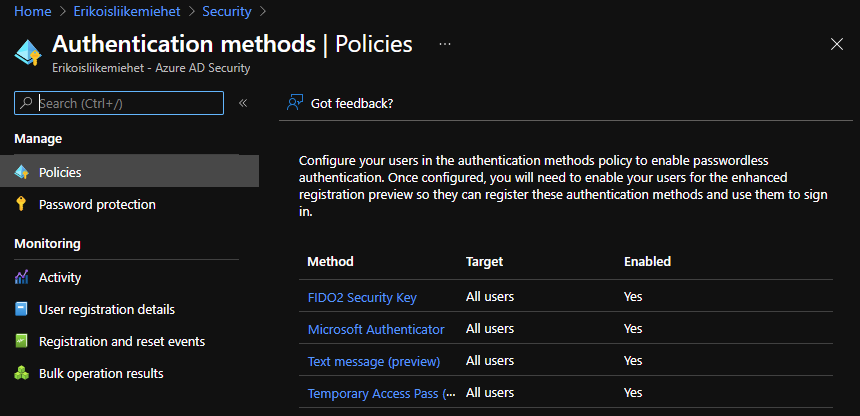
Deploying password-replacement offerings, as technical thing, is very easy if one is cloud only and easy in hybrid scenarios. Just enable passwordless options in your Azure AD and start testing. After this, end user manages their authentication methods in My Sign-Ins (microsoft.com)
It’s all about the process
When we are thinking on onboarding new user to company IT services the workflow could be:
- Receive new laptop via mail to home
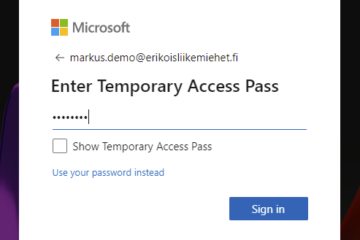
- Call to SD, authenticate and get Temporary Access Pass (TAP) valid for 8 hours. (Read more about TAP: The Magic of Temporary Access Pass – Bloggerz.cloud)
- Use TAP to login to autopilot enabled workstation and enroll to Windows Hello for Business
- Enroll blank (or existing) FIDO2 key to one’s account
- Use same TAP to setup Authenticator on the phone
This is something that can be customized to fit company’s Welcome process.
Want to learn more? There are more information available from Microsoft (Use passwordless authentication to improve security – Microsoft Security).
I will also post more real-life example very near future. While waiting, please remove password from your Microsoft Account: Introducing password removal for Microsoft Accounts – Microsoft Tech Community

1 Comment
Go passswordless in break the glass account - Bloggerz.cloud · 03.11.2021 at 22.58
[…] More information about planning and managing emergency access can be found from: Manage emergency access admin accounts – Azure AD | Microsoft Docs and more information about going passwordless can be found from my previous blog: https://bloggerz.cloud/2021/10/25/life-without-passwords/ […]