TL;DR; Easiest way to really secure your Break the Glass account is use FIDO2 security key and store the key in the physical safe.
Having way to login to Azure AD management plane after configuration mistake or during technical hiccup is something that every organization should address and plan. Creating account that can be used during emergency can save your day in the future.
Currently most of you creates account with long and complex password that is placed in safe, maybe even in two parts, and that account is excluded from all security controls namely Conditional Access Policies. Excluding from policies is needed as there might be configuration mistake or technical problem in enforced MFA method. Not enforcing MFA could potentially create security issue although use of this account creates alert – right?
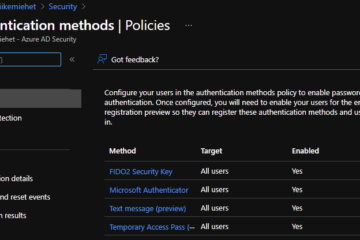
FIDO2 Security key to rescue!
Why to use FIDO2 security key for authentication for break the glass accounts:
- It has native two factor authentication (2FA): You need to have the key and know the PIN.
- As native 2FA, can be bypassed on all Conditional Access rules and still have more security than just using username and password.
- Can be placed in real life safe. Other 2FA methods are harder to store in safe. PIN can be stored in other location if needed.
- Same account can have multiple keys placed in different locations.

When FIDO2 security keys are in use, you should create very long and complex password for that account and forgot that instantly, as there is no way to remove password from account – yet. Plan also key rotation, that could even be automatically happening and no human should know that.
Remember also to create alerting rules when break the glass account is used as it should be normally used. This is commonly forgotten.
More information about planning and managing emergency access can be found from: Manage emergency access admin accounts – Azure AD | Microsoft Docs and more information about going passwordless can be found from my previous blog: https://bloggerz.cloud/2021/10/25/life-without-passwords/

0 Comments