Once upon a time (not so long ago) Data Loss Prevention (DLP) was a feature in Exchange and Exchange Online and would only affect mail flow. Nowadays the same technology has been transferred upwards one layer and is now part of Office 365 Security & Compliance center and deployable to Sharepoint Online and Onedrive as well. Deploying DLP does not require any additional licenses to your Office 365 Enterprise E3 / E5 – subscription. In this blog I will show you some experiences and examples on why and how to deploy DLP policies and what is the end user experience when DLP policies are deployed.
The Why
First question is obviously why would you deploy DLP policies? First of all you need to know what you can accomplish with them. Most common use scenario is to prevent sending or sharing of sensitive information to external recipients. With basic DLP templates you can recognize for example the following information from email and/or documents and configure policies accordingly:
- National ID
- IBAN number
- Passport number
You probably have a written policy in place and your end users informed that you should not have any of these examples written in email messages let alone in email messages that are sent to external recipients. DLP policies can help you accomplishing this. DLP Policies can be targeted to distribution groups allowing you to do some experimenting and piloting before deploying organization-wide. More of this in “The How” section of this post.
The What
At this point you are probably wondering how deploying DLP policies will affect end users and what is the end user experience when using them. First of all I will tell you that it is possible to allow users to override the policy. This will allow end users to send the email even though it contains sensitive information. Users will get notified with a popup so they will be informed that they should consider whether or not to send the message. The decision is up to end user then whether to remove the information from message or override the policy and send the message regardless. Let´s take a look at actual screenshots here
In this example we use Outlook for web, but similar experience comes with Outlook client as well. User is trying to send an email with sensitive information to external recipient and will receive Policy tip saying that you should not send this email.
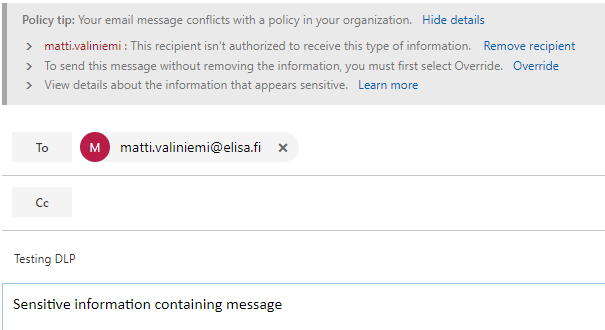
If the user ignores the message and sends the email without taking any additional actions they will receive information that the message was blocked. Outlook for Web shows this as a popup screen, Outlook client will send the information via email message.
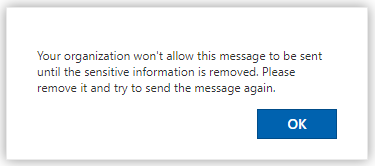
If the user has determined that they want to send this message regardless they have the option to override the rule by selecting “override” from the policy tip resulting in a different policy tip
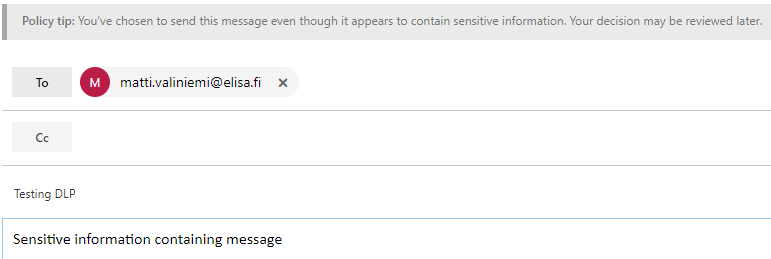
So the user is informed that they have chosen to do something that is not recommended and is against the company policy. After selecting “override” the user is then able to send the message. There are also possibilities to encrypt messages with Office 365 Message Encryption, but that is a topic for different post.
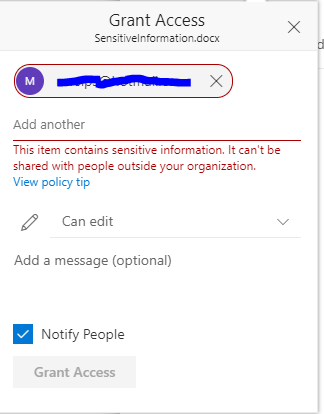
In Onedrive the end user experience is pretty similar. When sharing documents that contain sensitive information user will receive alert that this document cannot be shared and “Grant Access” button is greyed out
The How
Deploying DLP policies has been made easy and straightforward. You will however need Global Admin or Compliance Administrator permissions for the Office 365 tenant in order to configure the policies. Compliance Administrator permission are granted in Security & Compliance admin center.
After you a are granted the needed permissions then you will be able to see DLP as part of Security & Compliance center in Office 365 Admin portal
To configure the policy that was shown from end user perspective above we will go through the following steps:
- Create a new policy
- Select Custom policy Template
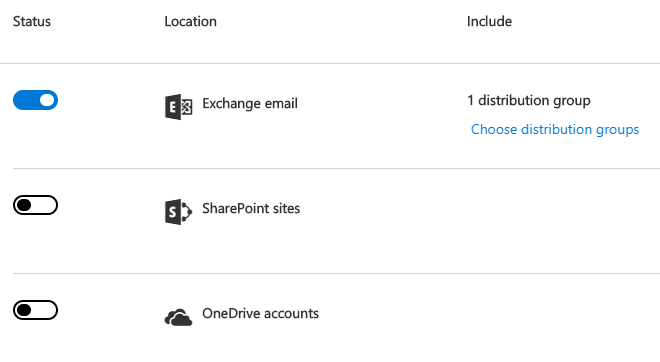
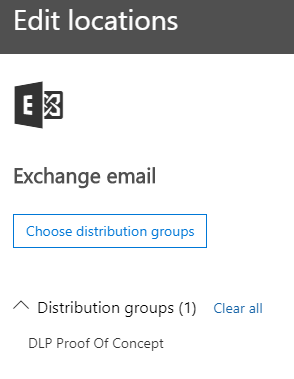
- Choose specific locations. This is very important because Exchange is the only location where you can target the policies per group. So if you dont want your policies to affect all users immediately you should choose Exchange as the only location and include only specific distribution group.
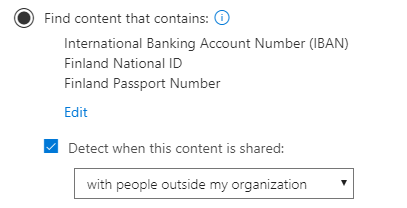
Next we will choose the types of content to protect. In this example I have chosen the following content and want to prevent external sharing :
Then we will configure the actions aka what to do if aforementioned content is detected. You can configure incident reports to be sent by email if you prefer, but these can also be obtained from Security & Compliance center and powershell.
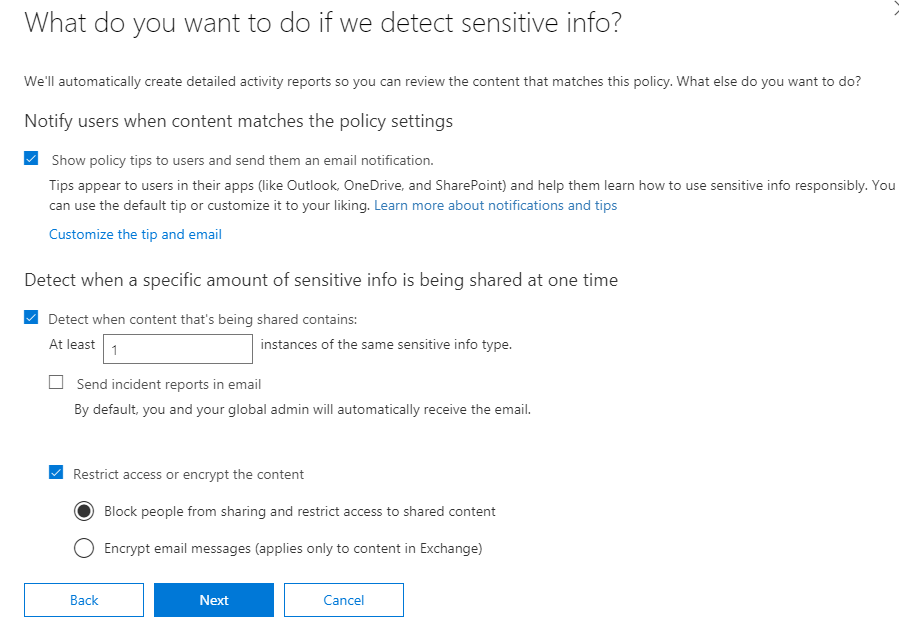
Then you will configure additional access permissions and override. I recommend letting users override the policy in the first phase so that you are not preventing anyone from doing his job.
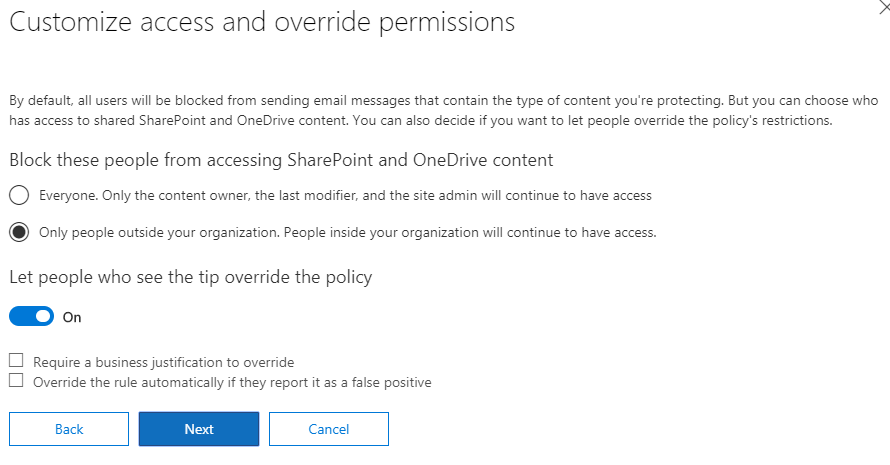
After configuring the policy you have the option to select whether or not you want to turn the policy on. I recommend turning it on right away since you have targeted it to specific distribution group, but you can obviously select otherwise if you prefer.
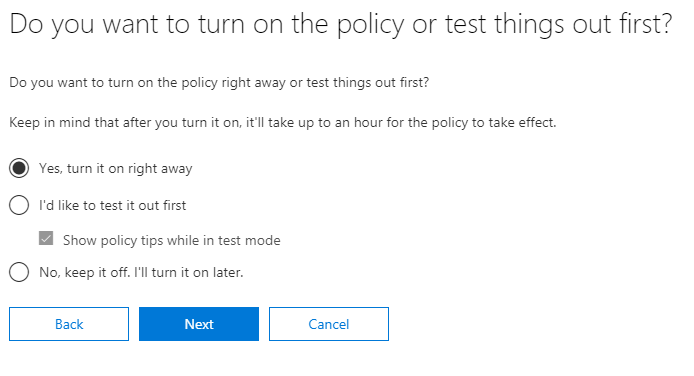
And that´s that. After you have completed the policy creation I recommend you check the settings and make sure that Low volume content and High volume content settings match and are configured accordingly. You can also customize policy tips that the users receive if you wish to. Also keep in mind that it can take some time before the policies are applied and users see the result.
After you have done some experimenting and piloting of the feature you can then deploy it to all users. I recommend deploying to Exchange first and then see how it affects your end users everyday work. One thing that you should consider is the fact that override requires user action. This means that if you have an application or service that is sending email “as” users they will not be able to use override and if the messages contain sensitive information and are sent to external recipients they will be blocked.
If you are interested in classifying data and messages and basing DLP policies on classification instead of content detection you should look into Azure Information Protection which is part of Enterprise Mobility & Security – packages.

2 Comments
John Jessen · 03.06.2019 at 00.50
Hi, does this require an E3 license or E5 license for people incorporated under MS DLP policies?
Markus Lintuala · 12.10.2019 at 15.55
Hi John! Sorry about the late answer, but DLP is included in Exchange Online Plan 2 which is part of both Office E3 and Office E5.