Microsoft’s VDI solution from Azure has been almost six months in public preview phase. I have completed several successful customer experiments and proof of concepts with it in EMEA area, while the whole publishing endpoints are still only in US region. Customer’s are waiting a lot of GA and the publishing endpoint availability to be launched in EMEA.
I will write couple of useful tips and tricks here that I have found during my testings and pilots. Feel free to comment and share this post!
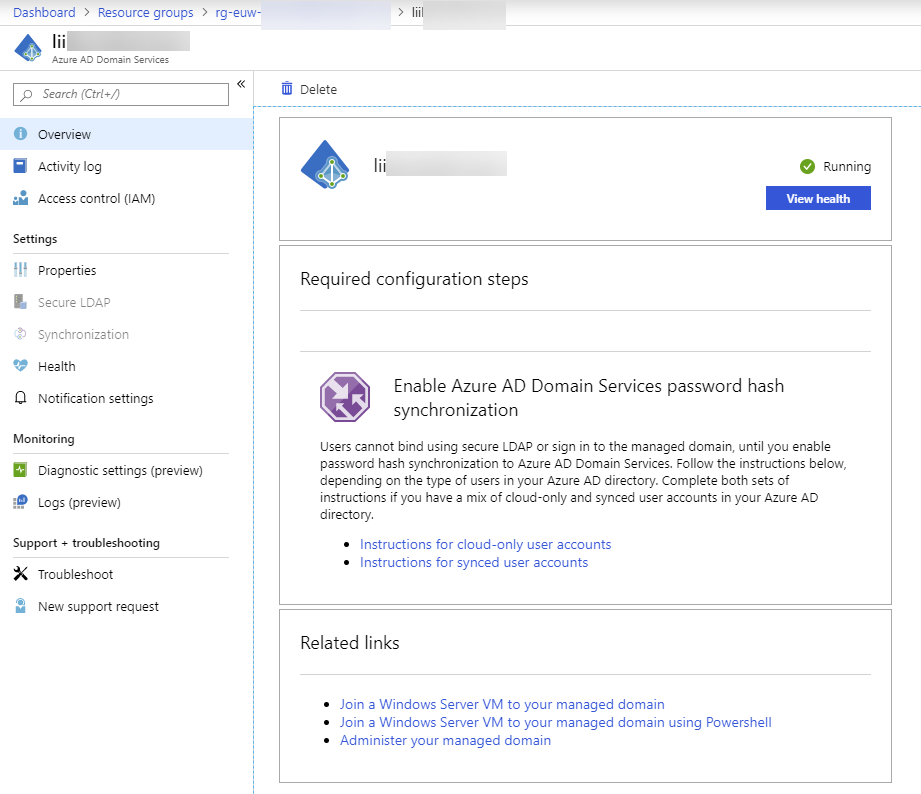
Azure AD Domain Services
If you have only workstations in workgroup (hope not) or Azure AD joined workstations without any on-premises Active Directory and you would like to use Windows Virtual Desktop, you have to create the AD DS somehow. Windows Virtual Desktop is currently supporting only Active Directory Domain Services joined workstations and servers in a session host role. This means that if you don’t have AD DS, you have to create it for Windows Virtual Desktop.
If Windows Virtual Desktop is the only thing why you need AD DS, I encourage you to use Azure AD Domain Services. AAD DS has been available several years, but there hasn’t been so many use cases for it before Windows Virtual Desktop.
There are Pros and Cons when using Azure AD Domain Services. I have listed those below from my opinion.
Pros
- You don’t have to maintain domain controllers
- You get traditional group policies for management
- Automatic user and group synchronization between Azure AD and Azure AD Domain Services
- Easy to deploy and manage
- High-Availability implemented by Microsoft
Cons
- You can’t use some AD related services with Azure AD Domain Services for example PKI or NPS server
- Problems of traditional AD DS
- LDAP related challenges
For more information about the Azure AD Domain Service, please refer Microsoft’s documentation.
FSLogix for profile management
When using virtualized end-user environments there are always user profiles that should roam through all pooled session hosts. If user’s profile is large, it will take a lot of time to copy files over the network for later on usage.
In the end of 2018 Microsoft acquired a company called FSLogix. FSLogix has several tools to help profile and application management especially in virtualized envrionments. In Windows Virtual Desktop context, the most valuable product from FSLogix is Profile Containers.
Profile Container packs user’s profile to VHD(X) file and stores it in a traditional File share. When user logs on to the session host, VHD(X) is mounted through the network for profile usage and de-mounted, when user logs off from the session.
FSLogix provides also extended caching mechanism called Cloud Cache, to reduce network traffic by caching profile files to the local machine. It has also capabilities for multiple sessions at a time, which is the basic requirement for tool like this. What is the best of this, FSLogix is licensed through other bundels, so you don’t need extra licenses for that. When writing this (5.9.2019) you are allowed to use FSLogix components if you have one of next licenses:
- Microsoft 365 E3/E5
- Microsoft 365 A3/A5/ Student Use Benefits
- Microsoft 365 F1
- Microsoft 365 Business
- Windows 10 Enterprise E3/E5
- Windows 10 Education A3/A5
- Windows 10 VDA per user
- Remote Desktop Services (RDS) Client Access License (CAL)
- Remote Desktop Services (RDS) Subscriber Access License (SAL)
Check the latest license requirements from Microsoft’s documentation.
Storing the FSLogix VHD(X)
There are couple of scenarios where you can store your FSLogix Container depending of your infrastructure. If you have Azure AD Domain Services, I encourage you to use Azure Files and if traditional Active Directory Domain Services, you have to use traditional file server, which is shame that Azure Files does not have yet support for Active Directory Domain Services. Maybe some day..
Either or, you need a folder to be shared over SMB and appropriate NTFS-permissions for it.
| User | Folder | Permissions |
| WVD Users | This Folder Only | Modify |
| Creator / Owner | Subfolders and Files Only | Modify |
| Administrators | This Folder, Subfolders, and Files | Full Control |
Azure AD Domain Services
When using Azure AD Domain Services, it’s the easiest to store VHD(X)-files in Azure Storage Account. How to configure the Azure Storage Account and Azure Files for FSLogix usage use the Microsoft’s documentation to complete the configuration. Remember the folder NTFS-permissions as described above!
Active Directory Domain Services
When using Active Directory Domain Services, you can’t integrate Azure Storage Account NTFS-permissions to it. Create a file server and share a folder with appropriate NTFS-permissions as described earlier for it. I suggest you to create the server to Azure so it would be really close session hosts.
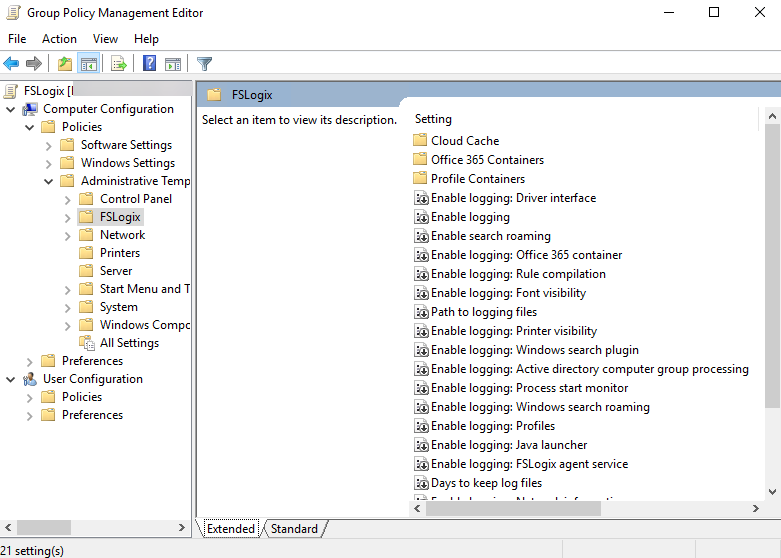
Group Policy Templates
To configure requried settings for session hosts, documentation says to use specific registry keys. In stead of updating straight registry, I suggest to use Group Policy Templates which are included in the FSLogix installation zip-archive.
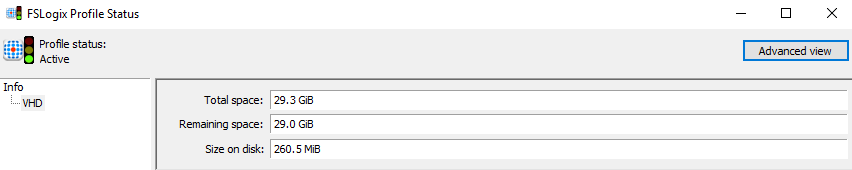
Frxtray.exe
When you have installed FSLogix client to your session host, you find a nice tool called Frxtray.exe. Use this tool to see traffic lights about the profile status, logs for troubleshooting and much more. Frxtray.exe is located in C:\Program Files\FSLogix\Apps\frxtray.exe if you used the default installation location for FSLogix client.
Provide Win32 applications for externals
One of the use cases for Windows Virtual Desktop is publish applications and desktops to external users. If you are using Windows 10 as a session host, you have to have licenses for external users also to use it (which normally does not have Windows licenses in your environment). If you use Server based SKU e.g. Windows Server 2016 for session host, you need only RDS Cal’s as normally. Less license costs for your external partners!
Session host with external GPU
As Windows Virtual Desktop is only a way to use Virtual Machines resources in Azure environment, you can use any size of them as a session host. One way is to use NV- or NC-series virtual machines which has an external graphic card for work loads that requires it (e.g. Video or CAD-rendering, editing and so on).
When you use virtual machine with a graphic card, it is not used in Remote Desktop Sessions automatically. To get graphic card working correctly in Remote Desktop Sessions, turn next Group Policy setting Enabled for those session hosts:
- Computer Configuration\Administrative Templates\Windows Components\Remote Desktop Services\Remote Desktop Session Host\Remote Session Environment
- Use the hardware default graphics adapter for all Remote Desktop Services sessions = Enabled
More than one administrator
When there are more than one administrator for RDS tenant, you should give tenant owner permissions to them as easy way as possible. The best way to achieve this is that create a AAD Group e.g. WVDTenantOwners and give Owner role for that specific group.
#Get AzureAD Group $group = Get-AzureADGroup -SearchString "WVDTenantOwners" #Make the role assignment New-RdsRoleAssignment -RoleDefinitionName "RDS Owner" -GroupObjectId $group.ObjectId -TenantGroupName "MyWVDTenantGroup" -TenantName "MyWVDTenant"
Use cases
There are plenty of different use cases for Windows Virtual Desktop from external partners to field engineers. The coolest use case in my opinion is Samsung smart phone as the only device for end user. Samsung phone has own desktop experience called Samsung DeX. You can start it by connecting your device to the HDMI-monitor or Samsung DeX docking station (which has HDMI port to the separate monitor). Connect mouse, keyboard and bluetooth headset to your phone and you can start fully functional Windows 10 Enterprise to the external monitor from your phone. How cool is that!! You can even edit your videos or CAD drawings with your device just without high performance (and heavy) laptop or desktop.

Test and demo environment
When running test or demo environment you want to ramp down all extra costs and still stay as maintained as possible with your infrastructure. There are several things that I have in my demo environment to maintain the infrastructure automatically.
Azure Automation Update Management
I have one Azure Automation Account to manage Updates for my session hosts. That’s really powerful and free update management solution for single environment requirements.
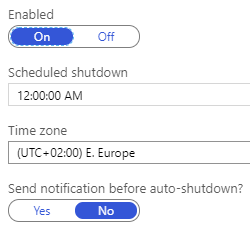
Auto Shutdown
I shut down my virtual machines when I don’t need those and VM’s are going to be also de-allocated, so only cost is the storage. If I don’t remember to shut down machines, those will be automatically turned off at midnight every day. Less expenses.
Starting of demo environment
I want also to start my demo environment with a single button, so I’ve created a button to call Azure Automation script to turn on the demo environment. I use also schedule to turn them on once in a week for update management purposes.
Summary
Conclusion after several PoCs is clearly that this works as expected and Windows Virtual Desktop is enough for many use cases when using VDI- or virtualized application environments. The best thing is that the price point for this solution is really friendly and encourages to use it!

2 Comments
Andy Mac · 07.11.2020 at 02.36
Really great article. You spoke about AADDS pros/cons, i just implemented WVD+AADDS (no on-prem AD). The biggest con is not realising there is no seamless SSO, users have to login to each app individually (OneDrive, Outlook, Teams, Edge), which seems strange for a cloud only solution. Hopefully future realises will resolve this.
Markus Lintuala · 13.11.2020 at 23.06
Hi Andy,
Truly AADDS is in my opinion an extension for AAD to continue support for standard legacy apps that requires LDAPS. For a security reasons I would leave that away and prefer AAD, but AAD only is not (at least yet) supported. I’m waiting much more support for AAD joined devices without Windows Server AD.