Executive summary: Do you lock your datacenter with old and poorly protected keys eg. Abloy Classic? Yup, me neither. You need to start enforcing multifactor authentication for privileged actions and/or accounts. Like yesterday.
The Problem
Protecting admin interfaces is crucial as we know that if someone gets to stand next to the server, that server should be treated as compromised. We are keeping tight track on who can walk in to our datacenter, but why are we not doing the same for datacenters in cloud? I come across customers that have read access to the Azure subscriptions for accounts that don’t use multifactor authentication (MFA) on daily basis. Most of the cases are even worse: Admin account can login without MFA and perform subscription owner tasks. I’m quite surprised that nothing major has hit the fan .. yet.

The same goes with f.ex. Office 365 admin portals. A year ago a study stated that only 20% of organizations are using multifactor authentication for their admin accounts. The number is even lower if we are talking about regular accounts that can still reveal business critical information or at least cause a lot of harm and extra work while cleaning after the account has been compromised.
The Cure
The easiest way to start protecting your accounts is to enable Azure AD Security Defaults or, if you have the licenses and skills, build a similar solution using Conditional Access rules. Always require MFA if the user is privileged or trying to access privileged resources eg. login to portal.azure.com or use Azure CLI.
Security Defaults are an easy and robust way to start protecting your environment. It will enforce MFA registration for all users (useful also in self-service password reset case) and enforce MFA for privileged users and actions. It will also block legacy protocols and ask for MFA from regular users if there is something fishy in the login.
How-to-documentation can be found from: https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/concept-fundamentals-security-defaults
More information about Conditional Access can be found around bloggerz.cloud, for example starting from here: https://bloggerz.cloud/2018/12/26/conditional-access-are-you-really-getting-the-most-out-of-it/
Call for action
Please take 3 minutes of your time and enable security defaults now or implement similar rules in conditional access.
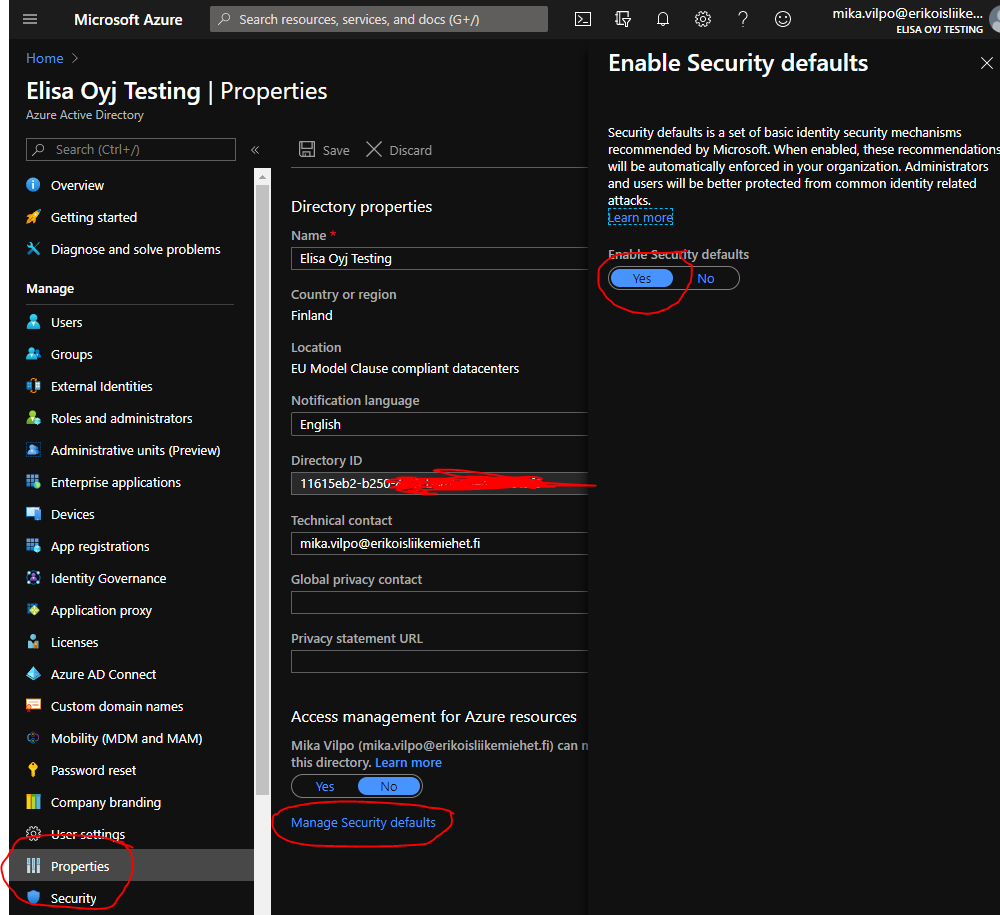
Yes, it is that simple. Do it now. If you are using Conditional Access it will take little time, but do it anyway. Then grab a beer and enjoy your life being little more secure.

0 Comments