After couple of weeks spring version of Microsoft Ignite is in the calendar and a lot of new announcements (at least I believe so). In the beginning of this week I noticed a new Authentication method in Azure AD Portal called Temporary Access Pass. On Monday there wasn’t any documentation available, but now there is! I believe it is going to be launched officially in Ignite. But of course I could look it little bit out before that 😉
What is Temporary Access Pass
Temporary Access Pass is a temporary access code for end user to authenticate without a multi-factor authentication (limited time only and once only if required). I have already couple of use cases for Temporary Access Pass:
- Enrolling a mobile to Intune in single-app mode has been a problem since you can’t give a MFA with a mobile in single app mode. More info about these caveats from another post
- If your company is already passwordless, you can sign in with a Temporary Access Pass for FIDO2 key registration!
Sounds perfect! 🎉
Configurations
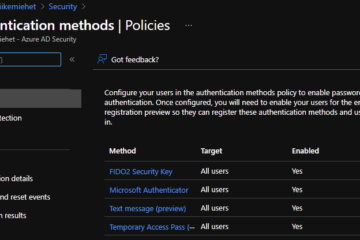
You can enable the Temporary Access Pass for selected users or all users under authentications methods from Azure Portal.
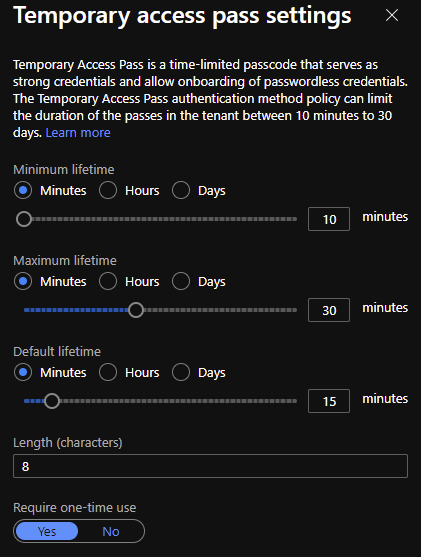
There are couple of settings to set up. I suggest to turn down lifetimes and turn on Require one-time use setting, to enable just temporary access for end-user.
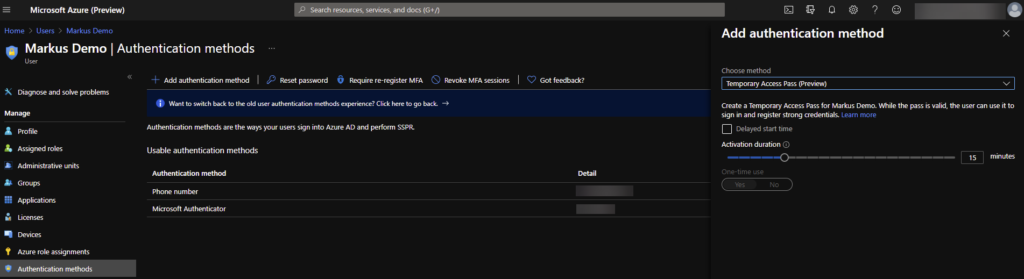
Creating a Temporary Access Pass
If you try to create a Temporary Access Pass for user under Azure AD portal you can’t find it from there. Instead of using https://portal.azure.com use https://preview.portal.azure.com. This will be in GA-portal surely later on.
Under user own authentication methods select add authentication method and as a method choose Temporary Access Pass (Preview). You can also select a delayed start time for example first time sign-in for a new user.
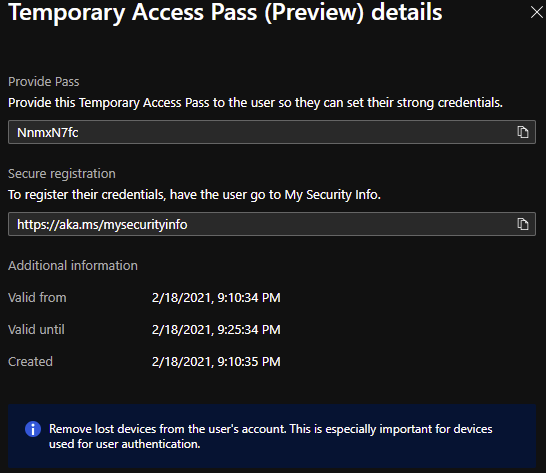
Settings that you can manage are related to the tenant-level settings that you set up already in Azure AD side. After selecting Add you see the pass that is provided for user.
It looks You can complete this creation also over API, so feel free to integrate it to your own systems. 😉
Just send a POST query with {} in body (or specify options to there) to https://graph.microsoft.com/beta/users/<user-principal-name-or-object-id>/authentication/temporaryAccessPassMethods
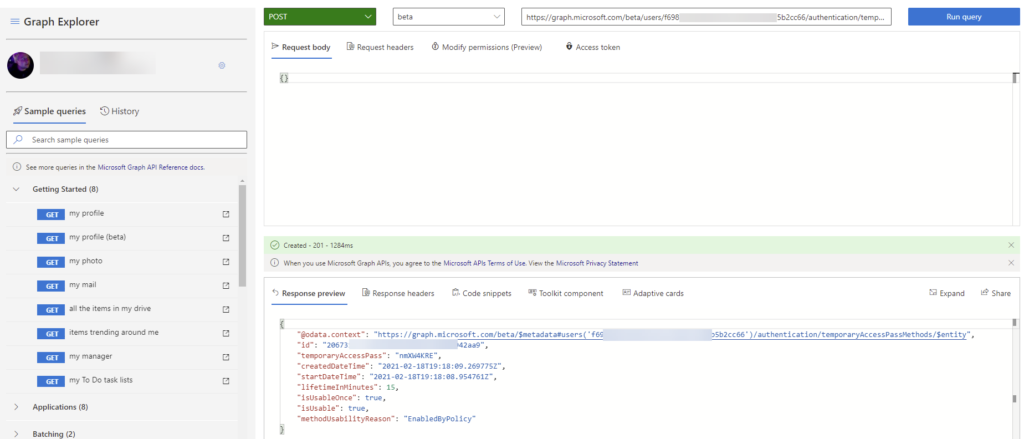
You need UserAuthenticationMethod.ReadWrite.All permissions to complete this. Permissions described more in the documentation.
End-user side
How does it look and feel then?
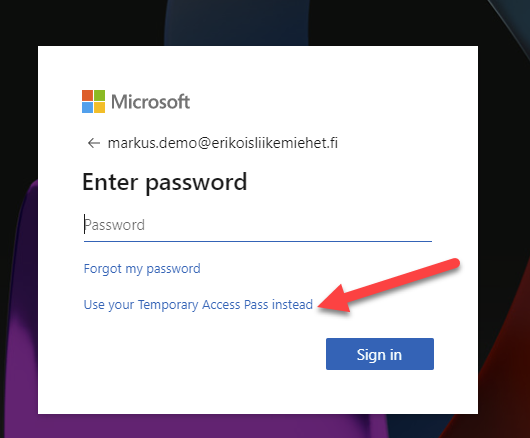
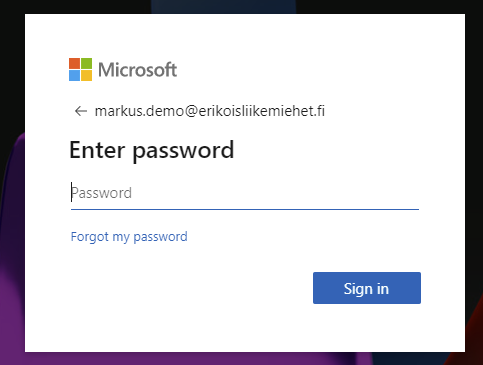
You write your username to the login form and select Next. Now you see (if Temporary Access Pass is created and active for you) User your Temporary Access Pass instead. Select it.
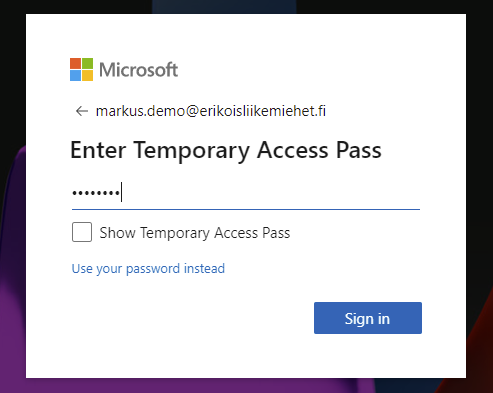
You enter the passcode now to the form and select Sign in.
And you are happily in without a MFA.
If your time runs out or you selected Require one-time use in settings, you can’t see the Temporary Access Pass option any more in sign-in form.
Conclusion
Many years I have waited this option. Now it is there. It is working and I am really really really happy 🎉

8 Comments
Anonymous · 11.03.2021 at 19.53
Very nice presentation !!!
two architectural point to clarify, though.
When the end-user is ready to register FIDO2 or WHfB, he has to collect the TAP from helpdesk or manager through any out-of-band mechanism, may be phone-call.
That means organization has to keep somebody standby to cater TAP to the end-users.
And secondly, how do I prove myself to my manager so that he remains confident that he is not giving away TAP to some rogue party ?
Markus Lintuala · 31.03.2021 at 14.59
Hi Anonymous 😀
I’m glad that you asked about this. You can get the TAP from AAD with API’s without manual work. Another question is, how do you deliver it for the end user who asks it confidentially – through manager or something else?
I think that the perfect solution for this would be that end user provides a personal authentication based on credential that is issued by national authorities to get the TAP. Many countries have already a way to provide an authentication digitally. Problem is that you have to have some kind of identifier on account that corresponds towards the national identifier and it is not a perfect either. Also every country has little bit different kind of the identification. In the future Verifiable Credentials could be something to investigate. Currently there is not a 100% full proof way to do it, but compared to current world, it’s same with passwords. When a person starts for example in a new workplace he or she will get the first password often from the manager.
mombu mombu · 05.04.2021 at 19.58
what AAD license P1 or P2 is required for TAP?
Markus Lintuala · 05.04.2021 at 20.28
Hi Mombu,
There is not clearly documented license requirement for TAP. As it is part of Passwordless solution, I would go forward with its license requirements stated here https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-authentication-passwordless-deployment#licensing. So because passwordless authentication does not require any additional licences, I don’t see that TAP requires either. I’ve not confirmed this from Microsoft since it is still in preview and license etc. requirements might change before the GA.
mombu mombu · 05.04.2021 at 20.47
Thank you, Markus!
Robert McClellan · 07.12.2021 at 19.25
What if logging into Microsoft doesn’t ask for a password?
Markus Lintuala · 13.12.2021 at 22.39
Hi Robert,
That’s the whole point in Passwordless that you do not use passwords! 🙂
Life without passwords - Bloggerz.cloud · 25.10.2021 at 10.34
[…] Call to SD, authenticate and get Temporary Access Pass (TAP) valid for 8 hours. (Read more about TAP: The Magic of Temporary Access Pass – Bloggerz.cloud) […]