After several customer implementations I wanted to discuss about Microsoft Intune MDM automatic enrollment methods and their small caveats related to Multi-Factor Authentication (MFA). We all know the importance of MFA in today’s cloud security and using it with Intune enrollments is a really nice security addition in the process.
You have a lot of options when choosing your Intune MDM strategy and enrollment methods. I recommend you to take a look at the following Microsoft docs when choosing the right strategy for your organization.
The planning guide covers more than just enrollment options but it’s a really good read. You can read my colleague’s posts about setting up Apple DEP, Samsung KME and Google Zero Touch.
The issue I want to discuss is related to the combination of automatic enrollment methods and MFA. As of today Apple DEP with Single App Mode and Android Fully Managed devices using Samsung KME and Google Zero Touch are affected with the issue. I will also explain another known issue with Apple DEP and Single App Mode.
Multi-Factor Authentication and Apple DEP
To empower your users with their new Apple devices you really want to use Single App Mode in your Apple enrollment profile. This configuration basically locks the iOS after the first launch and automatically enrolls the device to Microsoft Intune without any complicated user actions. User is not able to access the phone before the setup is ready.
There is a (slightly confusing) documentation about configuring Apple enrollment profile here. You need to understand the different options and their limitations while choosing the best combination for you.
The documentation tells that if you want to use Multi-Factor Authentication you must authenticate the users in Company Portal instead of Apple Setup Assistant. Fair enough.
Which came first, the MFA or the Single App Mode?
Lets imagine a new employee starts and unlocks their shiny Apple iPhone. He/she is guided through the process and when Single App Mode launches and Company Portal wants you to authenticate using Multi-Factor Authentication; how do you perform the MFA as the user’s device is currently locked in the Single App Mode?
Workarounds
I honestly think you have three options and you need to choose the right one based on what your organization requirements might be regarding security and MFA.
Disable MFA from Microsoft Intune Enrollment
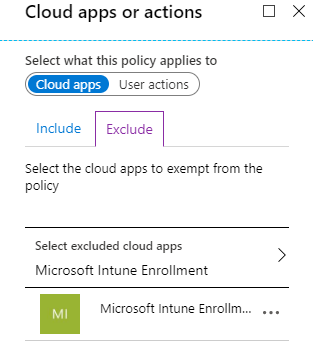
Yes. You could do this for your enrolling users with Azure AD Conditional Access by excluding Microsoft Intune Enrollment from the Cloud apps. This is equivalent to the Intune Company Portal that performs your Apple device’s enrollment. This reduces your security but improves your productivity and allows you to use Single App Mode to make sure your enrollments are consistent around the organization.
Disable MFA from the user when enrolling
You could temporarily disable MFA from the enrolling user each time they unlock their new device and enrolls it. This adds a lot of administrative overhead but it could be an option for a smaller organization. In organizations with tens or hundreds of thousand users it could be unacceptable.
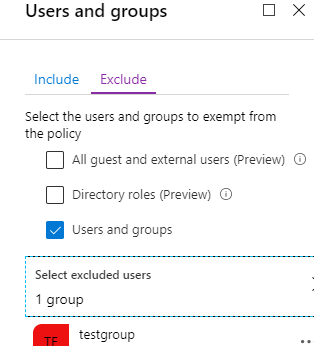
You might also want to consider one time bypass for MFA.
Advice the user to perform MFA from another device
I have done and seen this as well but you surely ain’t making new friends. I consider this for the high security organizations when you can’t make any exceptions to MFA policies. You need to advise the user to perform MFA with their previous device and/or their personal device to enroll the new company device.
Apple DEP and “Guided Access app unavailable”
This one is a bugger. This little informative pop-up should be there for less than a minute during the Single App Mode enrollment. At least according to Microsoft. The thing is that there is a known bug in Intune which can cause this screen to stay there forever. Yes, forever.
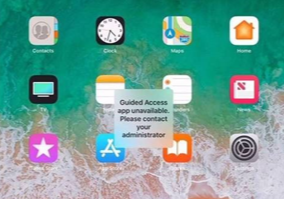
I have contacted both Apple and Microsoft about this issue and just recently I found out that this indeed is a bug in Intune and the product group is still trying to find a solution. The fix was supposed to be released in Intune service release 2001 but it’s still there and Microsoft has confirmed this to me 02/2020.
Workarounds
There are couple workarounds for this issue and you can choose between these two.
Reset the phone like you mean it
I’m serious. You can keep resetting the phone until one day it works and the enrollment succeeds. It can require one reset, ten resets or sometimes you’re lucky and you don’t bump in to this issue at all. Experience has shown that if you leave the phone to “Guided Access app unavailable” screen and just wait – it might continue at some point by itself.
Don’t use Single App Mode
This is what Microsoft recommended for me but it’s frustrating because this is the only thing I want to use when enrolling with Apple DEP. The issue appears to be that the application (Company Portal) is unable to get a VPP license in the locked state and the official workaround is to enroll the device without the option enabled. VPP on the other hand is required to download the Company Portal app on behalf of your user.
Multi-Factor Authentication, Samsung KME, Google Zero Touch and Android Fully Managed devices
While in Apple DEP enrollments you have an option to exclude MFA from the enrollment process – with Android Fully Managed this is a whole other story because Intune Company Portal alone isn’t used anymore. There are also applications called Microsoft Intune and MIcrosoft Intune Company Portal which the Android Fully Managed devices use.

The issue with the latest Microsoft Intune Company Portal app is that it doesn’t exist in the Conditional Access applications so you can’t exclude it. This brings us to the chicken or the egg problem during the enrollment.
Please note that this issue is relevant only if you have other Conditional Access policies which applies to All cloud apps. Many organization does this instead of creating application specific policies.
Workarounds
There are three workarounds for this which you might want to consider using. These are pretty much the same workarounds than with Apple DEP issue except you can’t currently exclude the cloud app from Conditional Access.
Disable MFA from the user when enrolling
You could temporarily disable MFA from the enrolling user each time they unlock their new device and enrolls it. This adds a lot of administrative overhead but it could be an option for a smaller organization. In organizations with tens or hundreds of thousand users it could be unacceptable.

You might also want to consider one time bypass for MFA.
Advice the user to perform MFA from another device
I have done and seen this as well but you surely ain’t making new friends. I consider this for the high security organizations when you can’t make any exceptions to MFA policies. You need to advise the user to perform MFA with their previous device and/or their personal device to enroll the new company device.
Re-model your Conditional Access policies
Like said, this only affects you if you have Conditional Access policies that will hit your mobile device users and all cloud apps. If this is the situation you could turn this around and apply the policy to only chosen cloud apps instead of all.
I am positive that we are able to exclude this new app in the near future so you might want to hold your breath before building all the Conditional Access policies from the scratch.
Final words
In overall the automatic enrollment programs are really the way to go especially in a structured large organizations. You need to accept some caveats with the MFA and plan a strategy how to overcome these obstacles. As the Microsoft Intune capabilities and options keep growing really fast we might not have these issues tomorrow, but meanwhile this is how the cookie crumbles.



12 Comments
Colin · 03.09.2020 at 00.02
Thanks for the article. Excluding the Microsoft Intune Enrollment app doesn’t seem to work for me. Do you know if this has changed since your article?
Joni Nieminen · 17.09.2020 at 09.09
Hey!
There are currently two apps available for Intune in Conditional Access. The “old” Microsoft Intune Enrollment and the new Microsoft Intune which is used in Android’s Fully Managed enrollments for example. Can you briefly explain your scenario in which the exclusion doesn’t work? Also it’s worth checking the Azure AD sign-in logs for the user in question to see what Conditional Access policy he/she is being hit.
David Quiroz · 09.10.2020 at 21.09
Hi Joni – I have the same question as Colin. We use automatic enrollment for our iOS devices using single app mode (as described above) but excluding the Microsoft Intune Enrollment (old) or Microsoft Intune did not seem to work (tested this months ago and wondering if this has changed). Thanks!
Joni Nieminen · 10.02.2021 at 08.28
Regarding the Intune enrollment applications you might also see “Microsoft Intune Company Portal” which isn’t listed as a cloud application in Conditional Access. This can cause issues at certain enrollment phases.
About a year ago when I asked this from Microsoft support they told me to change the Conditional Access policy to be targeted to single applications instead of All cloud apps to avoid the issue. When you assign policies to “All cloud apps” you’re most likely going to bump into some weird issues due to not being able control exclusions. Microsoft doesn’t recommend using the “All cloud apps” assignments due to this reason although it’s a nice thing to cover everything.
They also suggested to disable MFA for the enrolling user prior the enrollment (which is obviously a huge administrative burden). Unfortunately I haven’t tried this recently myself but I will let you know once I know the complete behavior as of today.
Markus Lintuala · 18.02.2021 at 22.11
Single app mode can be used now with a temporary access pass: https://bloggerz.cloud/2021/02/18/temporary-access-pass-for-places-where-mfa-is-not-possible/
AC · 04.03.2021 at 22.49
Hi, is there a way to use phone app MFA code or app push for Microsoft Authenticator app instead of just PIN, Biometric or Bluetooth for second factor for Azure AD/Intune joined Windows 10 machines? I am able to do this during enrollment, but not after. I could’ve sworn I’ve seen this done before, but can’t find any information on it. Thanks
Joni Nieminen · 12.03.2021 at 08.36
Hey!
Basically that would require signing in using the Microsoft Authenticator app (see Sign in to your accounts using the Microsoft Authenticator app) but this is not (at least yet) supposed to be used for signing in to your computer. Microsoft still recommends using Windows Hello for this which you referred to yourself (at the end of Frequently asked questions).
You should take a look at other passwordless authentication scenarios which are currently supported but I’m afraid that authenticator app login to Windows computers is not yet supported.
Passwordless authentication scenarios
Choose a passwordless method
Ajay · 09.04.2021 at 16.59
Thanks for the article this helped explain quite a few things for me :). One thing that might be good to add to this article is if people are using Per User MFA and not conditional access MFA then the above wont apply to them. I tested this in my test environment and if MFA is enforced in the user page then conditional access policy to bypass it during enrolment wont work. Or atleast it didnt work for me but as soon as i disabled MFA in the user page and added the user to MFA in conditional access the bypass works great for iOS and Android.
Joni Nieminen · 30.04.2021 at 07.27
Hey Ajay and thanks for the feedback and your comment!
Darren · 05.05.2021 at 10.53
During non-single app mode user affinity enrolment with company portal app, is it possible the user flow can include MFA registration by pushing VPP Microsoft authenticator to the device?
Joni Nieminen · 27.05.2021 at 09.16
Hey Darren!
During the enrollment when MFA is required the user will be directed to register MFA automatically unless he/she hasn’t previously. During this registration experience the normal methods are available. If your question is whether the user can configure Authenticator app as his/her authentication method during the enrollment using the same device, I would say it’s at least quite difficult if impossible.
My general suggestion is to perform the enrollment MFA with another device if available easily or use the new Temporary Access Pass to finish the MFA and configure Authenticator app later.
Apple Dep Intune Company Portal - LoginWave · 22.03.2022 at 18.24
[…] 12. MFA and other caveats with Intune MDM automatic enrollment … […]