Introduction
In my previous post regarding planning of Conditional Access in your organization I wanted you to understand the different aspects of the policies.
I would like also recommend you to read my dear colleague’s post about Conditional Access generally and for what kind of threats it will protect you from.
Bare in mind that Conditional Access is just not about securing access to Microsoft Exchange Online (for example) – instead it is providing you a comprehensive control and protect across your whole cloud infrastructure.
I, myself, consider Conditional Access hand-in-hand with Multi-Factor Authentication (MFA) one of your best security features in Azure Active Directory.
I will remind you of the five principles I was talking about in my first part of this series:
Control your own employees with device-based access
Control your administrative accounts
Control your guest accounts
Control everything else possibly passing through the above
Last but not definitely the least, block legacy authentication including Exchange ActiveSync
Pre-requirements for the policies
I will shortly talk about the pre-requirements for the policies to fully take effect. Please note that you are able to implement most (or some) of the policies without these requirements but I strongly recommend that you plan and consider taking the full out of the product.
Hybrid Azure Active Directory join
You really need to hybrid join your existing on-premises AD devices to Azure AD if you already haven’t. This is a requirement for the device-based access to work properly.
Microsoft has made this much easier these days with Azure AD Connect and you can follow the instructions whether you’re using managed (Pass-through authentication, Password hash sync) or federated (ADFS) domains.
Enable Modern Authentication for your tenants
This is not yet again a requirement for most of the policies to work but it is strongly recommended to enable Modern Authentication for your Exchange Online and Skype for Business Online tenants.
This is also crucial when blocking legacy authentications.
You can read about Modern Authentication here and especially for Exchange and Skype below.
Enroll your mobile devices to Microsoft Intune
I will surely later talk to you a lot about mobile device management in Microsoft Intune but now just shortly: Enroll your organization’s mobile devices to Intune as it will provide you so many benefits together with Conditional Access and device-based controls.
To get started you can read about enrolling your devices to Microsoft Intune.
Create general exclusion groups
You need to exclude certain service accounts and non-interactive accounts from the policies. These could be your ERP system users sending out e-mails and for example your Azure AD Connect synchronization account.
Create an on-premises group and a cloud-only group in case you have such accounts in both environments.
Always exclude these two groups from all the rules.
Consider the use of different client apps
You might want to create separate rules for browser and client access as those two might have different access controls depending of your organization’s policies.
For example only client use is allowed from hybrid joined devices (company owned) and browser use is allowed with MFA (public devices).
Start testing with restricted groups
You should not apply the policies for all users first – instead use a test group and start expanding it and eventually switch the policies to affect all your desired users.
You start by going to Azure portal – Azure Active Directory – Conditional Access.
Policy for your own employees
This is a simple one as basically all of the rest are.
Create four new policies for client and browser use (two for mobile and two for client = workstation) as below.
- Assignments
- Apply this policy to the groups(s) for your own employees
- Exclude the previously mentioned groups for service accounts etc.
- Cloud apps
- Choose ‘All cloud apps‘
- Exclude any cloud apps you might have a fine-grained policy for
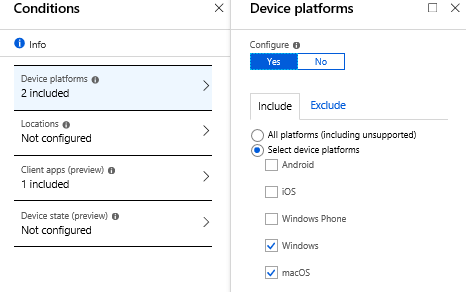
- Conditions
- For Device platforms choose whatever your organization is using
- For client use choose Windows / macOS
- For mobile use choose Android / iOS / Windows Phone
- For Device platforms choose whatever your organization is using
- For Client apps you choose either:
- Browser
- Mobile apps and desktop clients / Modern authentication clients
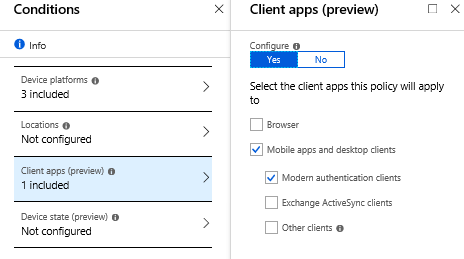
- Access controls
- Grant access based on whether it’s mobile or client use:
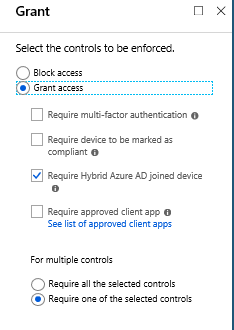
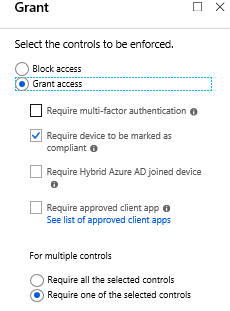
- Require device to be marked as compliant (Mobile / Intune)
- Require Hybrid Azure AD joined device (Client / Hybrid joined)
- Grant access based on whether it’s mobile or client use:
Policy for your own administrative accounts
For administrative accounts you can create just two policies. One for clients (workstation and mobile) and one for browsers (workstation and mobile).
Assign the policies to the groups which consists your administrative accounts and remember to exclude the general exclusion groups.
Otherwise it’s all the same policy as for your own employees except for access controls you want MFA every time.
- Access controls
- Require multi-factor authentication
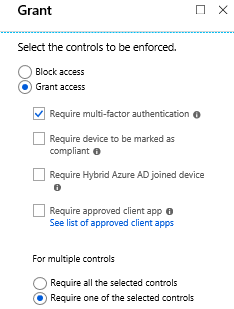
Enable the baseline policy
In addition to your own administrative accounts – do enable the baseline policy provided by Microsoft.
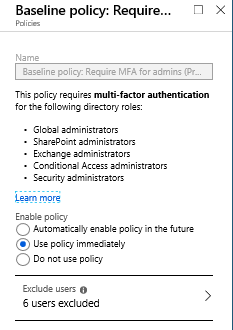
Exclude any backdoor accounts or other service accounts not used by actual personnel. These could be Cloud App Security accounts and/or such.
Policy for guest accounts
This is pretty much the same as administrative accounts except you assign it to ‘All guest users‘.
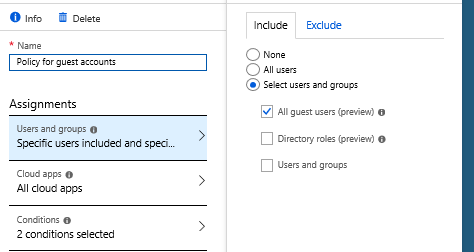
Create two policies for guests – one for client and one for browser use.
In the guest users policy you can choose ‘All platforms‘ in ‘Device platforms‘ condition. You also grant access only with MFA.
Policy for all (the other) users
To master the rest of the users accessing your organization’s cloud services you can finally create a policy that is assigned to ‘All users‘.
The trick here is to exclude all the previously configured assignments. And to repeat those are your own employees groups, your administrative accounts, guest users.
This policy can also have ‘All platforms‘ in ‘Device platforms‘ condition and you create two of them for clients and browsers.
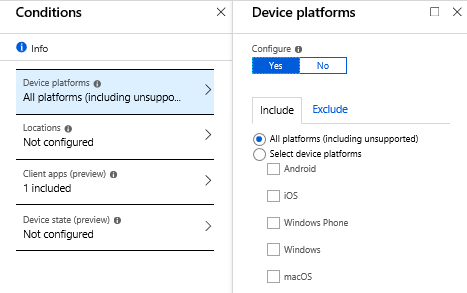
Policy for blocking Exchange ActiveSync
This is also a simple one. You can read more from Microsoft’s documentation.
- You don’t need any assignments.
- For Cloud apps choose Office 365 Exchange Online.
- For Conditions / Client apps choose
- Mobile apps and desktop clients / Exchange ActiveSync clients / Apply policy only to supported platforms
- For Access controls you simply block
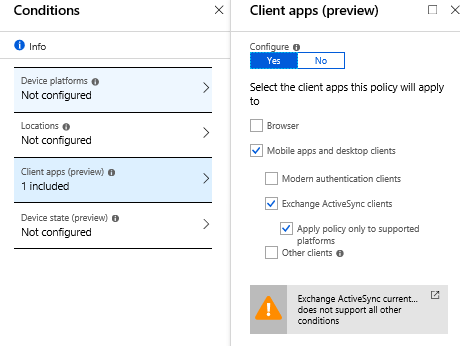
Please note that for example the lates iOS native mail clients use Modern Authentication by default so this doesn’t block those.
Policy for blocking legacy authentication
There are still some issues with applying this policy for everything and everyone. I suggest you be very careful with this one and only test it with a restricted group first.
I will later tell you about these issues and challenges more closely.
Regarding blocking the legacy authentication you can read it from Microsoft here.
- You don’t need to assign this to anyone
- Unless you are of course testing first
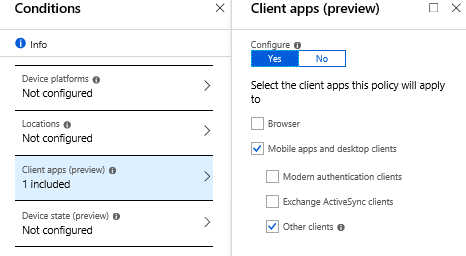
- Choose All cloud apps
- For Conditions / Client apps choose Mobile apps and desktop clients / Other clients
- For Access controls you simply block
Policy for Microsoft Intune enrollment
You really should enable Multi-Factor Authentication (MFA) when enrolling devices to your Microsoft Intune.
This is a security measure that controls only your own employees and trusted persons are enrolling their devices.
- Assign it to All users
- For Cloud apps choose Microsoft Intune Enrollment
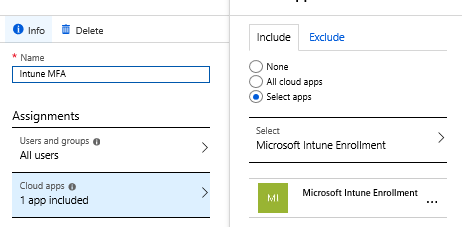
- You don’t need any conditions
- For Access controls choose
- Require multi-factor authentication
Final words
There you go – simple as that. Please remember this is just an example showing you how you can cover all the aspects when it comes to securing your cloud services and data.
You might have different needs and scenarios so please feel free to customize your own policies accordingly.
We will later cover you with more details about using sign-in logs to determine what is happening with Conditional Access policies and how to prepare for any undesired situations when enabling the policies.
Please comment and share this post – I would love to help you all with your challenges!

1 Comment
Conditional Access demystified, part 8: Resources and further references | Modern Workplace Blog · 26.05.2020 at 08.44
[…] Conditional Access – are you really getting the most out of it?, by Joni Nieminen – https://bloggerz.cloud/2019/01/02/conditional-access-are-you-really-getting-the-most-out-of-it-part-… […]